What is container technology? It involves consolidating applications and all their dependencies into a unified container. With containers, software development becomes faster, more efficient, and more versatile. To leverage the full benefits of containerization, you need to use popular tools like Docker container technology, which we’ll explain here.
This blog will dig into containerization and how containers fit into DevOps and CI/CD pipelines, as well as the best practices for security. We’ll address challenges, present use cases, and briefly discuss Docker container technology.
So, let’s explore Container Technology, this game-changing innovation in the tech world!
- What is Container Technology?
- Most Popular Containerization Tools
- Difference Between Containers and Virtual Machines (VMs)
- Benefits of Container Technology
- Security in Container Technology
- Challenges and Considerations in Container Technology
- Containerization Use cases
- Case Studies
- Conclusion
- Container technology FAQs
What is Container Technology
The core of modern Software Development and Deployment practices are Containers. They reflect a significant change in the way applications are packaged and run. We’ll delve further into the realm of Containers in this section.
What is Containerization?
Containerization is the practice and methodology behind Container Technology. It is the art of efficiently building, deploying, and maintaining Containers. Developers and Operations teams may use Containerization to take the idea behind Container Technology and turn it into a workable strategy for more effective and dependable software distribution.
The Development and Deployment of Applications using Container Technology has completely changed the way software is developed and managed. At its core, Container Technology is all about combining applications and all of the dependencies they require into a single Container.
Unlike traditional application deployment, Container Technology offers a standardized method where differences in computer environments and dependencies might cause problems. Thanks to the adoption of container technology, applications are no longer constrained by the host system’s traits. They are much more adaptive and portable as they carry their complete environment inside.
Applications are packaged into Containers via Containerization technology, and each has everything needed for an application to operate without an issue. This includes the configurations, runtime, libraries, and program code. Containerization transforms into a self-contained unit that is simple to move around, providing reliable performance and lowering deployment complexity.
Why is Container Technology Important?
Containers are important because they offer portability, scalability, and resource efficiency. Applications and their dependencies are contained in containers, ensuring that they function reliably in a variety of environments. This consistency simplifies the deployment process, reduces deployment complexity, and solves the frustrating “it works on my machine” issue.
Additionally, containers provide simple scalability, allowing applications to respond easily to changing workloads. They are more resource-efficient than traditional virtualization techniques because they share the host operating system kernel, which optimizes resource utilization.
Also, application container technology enables robust isolation, improving security and dependability. The software development lifecycle is accelerated by their easy integration into DevOps practices, while modularity and flexibility are boosted by their compliance with microservices architecture.
Containerization will help deploy Software more quickly and with more reliability and efficiency.
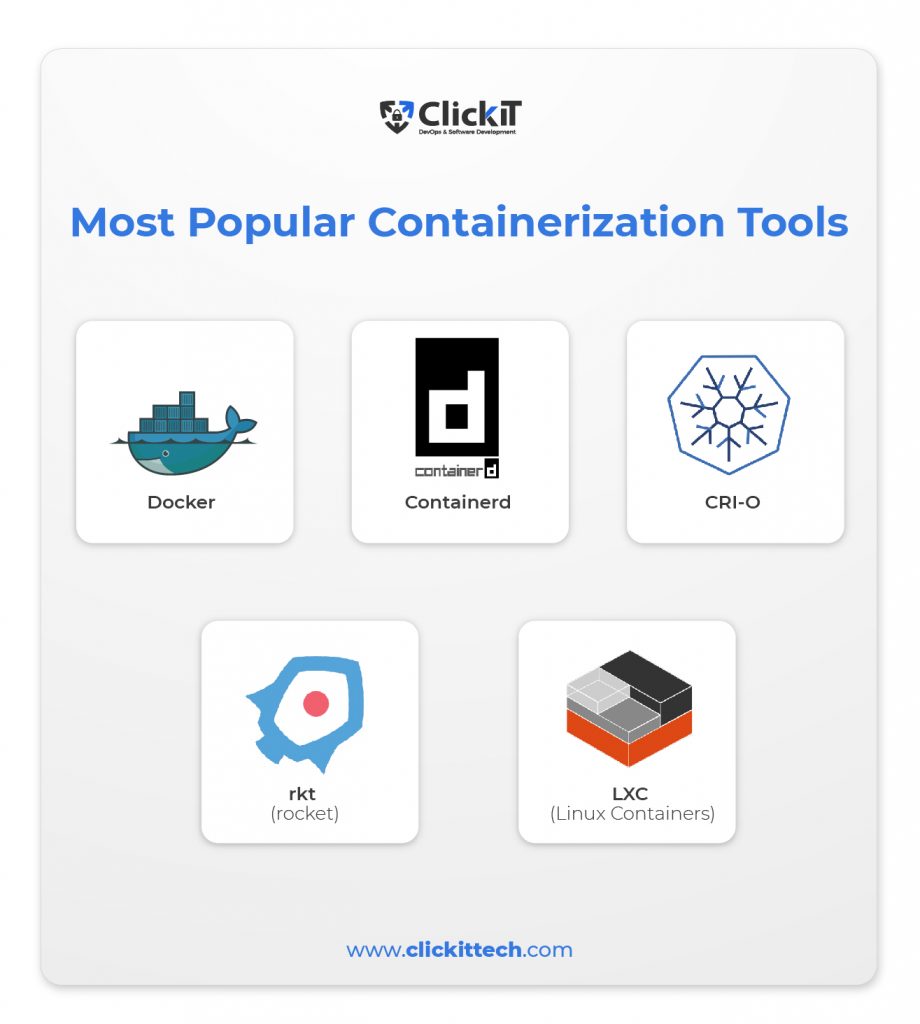
Most Popular Containerization Tools
In containerization, there is a set of powerful technologies at the core of the breakthrough that has completely changed software development and deployment.
Teams in operations and development can efficiently build, manage, and deploy containers thanks to these technologies. Some of the most well-liked containerization tools broadly embraced in the sector are listed below.
- Docker
- Containerd
- CRI-O
- rkt
- LXC
Docker
In many ways, Docker container technology is frequently the first name that comes to mind. Many developers and organizations now consider Docker to be the preferred containerization solution due to its broad appeal and influence on containerization technologies. It offers a complete platform for building, packaging, and distributing containers.
The user-friendly interface of Docker container technology and its large ecosystem of images and plugins have elevated it to the top of the list among developers and businesses all over the world.
Additionally, the large community support complements it and makes it a better choice for those seeking a robust containerization technology solution.
Read our blog about Docker use cases and watch our video Why use Docker (a real-life experience)
Containerd
Originally created by Docker container technology and then given to the Cloud Native Computing Foundation (CNCF), Containerd is a widely used container runtime. It provides a compact, effective runtime environment for containers and acts as a fundamental building block for container platforms and orchestrators.
CRI-O
CRI-O serves as an implementation of the Kubernetes CRI (Container Runtime Interface), facilitating the utilization of OCI (Open Container Initiative) compatible runtimes. This lightweight alternative offers an alternative to Docker container technology as the runtime for Kubernetes, enabling it to employ any OCI-compliant runtime for running pods. CRI-O is fully compatible with OCI container images and possesses the capability to pull from various container registries, providing a streamlined substitute for Docker, or rkt in the Kubernetes runtime environment.
rkt
Introduced by CoreOS in December 2014, the rkt project has undergone substantial growth and has garnered widespread adoption. Red Hat later contributed to this initiative for the Cloud Native Computing Foundation (CNCF). rkt, pronounced as “rocket,” serves as an application container technology engine purpose-built for contemporary production-oriented cloud-native environments.
As a command-line interface (CLI) tool, rkt facilitates the execution of application containers on Linux systems. Its core design principles revolve around security, composability, and adherence to industry standards.
It’s important to note that the project has reached its conclusion, and for additional details, you can visit the project’s GitHub repository at https://github.com/rkt/rkt.
LXC (Linux Containers)
LXC is a userspace interface for the Linux kernel containment features and an open-source container platform. It provides tools, templates, libraries, and language bindings. Thanks to a robust API and straightforward tools, LXC enables Linux users to create and maintain system or application containers with ease. LXC features a direct command-line interface that enhances the user experience while starting containers.
Discover the top 10 alternatives of Docker.
Difference Between Containers and Virtual Machines
The decision between Virtual Machines (VMs) and Containers is crucial in the constantly changing environment of IT infrastructure because it can have a big impact on how container technology applications are deployed and managed. Each approach has a different combination of benefits and drawbacks; therefore, it’s crucial to recognize the variations to make an informed decision.
In this section, we’ll explore the differences between Containers and Virtual Machines (VMs), revealing the isolation levels, resource efficiency, startup times, mobility, densities, and use cases.
Table Difference of Containers and VMs
| Aspect | Containers | Virtual Machines |
| Isolation Level | Containers offer isolation at the process level. On the host operating system, each container runs as a separate process. This provides good separation, but it’s not as strong as VMs. | VMs provide greater separation. A full guest operating system is running in each VM, increasing the level of separation between VM instances. |
| Resource Efficiency | Because they share the host OS kernel, containers are very resource-efficient. As a result, they have little overhead, which enables them to maximize resource use. | Since each VM comes with a full OS, VMs have a larger resource overhead. The use of several VMs on one host may put a load on its resources. |
| Startup Time | They don’t have to boot a complete OS so containers start very quickly—almost instantly. | They do have to boot a complete OS, so they generally start more slowly compared to containers |
| Portability | They include both the programme and its dependencies, containers are very portable. This ensures consistency across multiple environments. | Because of their greater size and resource requirements, VMs are less portable. |
| Density | Due to their lower resource overhead, containers allow a higher application instance density on a single host. | Due to their greater resource needs, VMs often have a lower density on a host. |
| Use Case | Containers are great in situations where quick scaling, flexibility, and resource optimization are required. DevOps techniques, cloud-native applications, and microservices architectures all frequently employ them. | VMs are appropriate for workloads that call for robust isolation, backward compatibility with legacy programmes, or the ability to run several operating systems on the same hardware. |
Benefits of Container Technology
Now that you know what is container technology, we will delve into the key benefits of container technology, exploring how it revolutionizes traditional development paradigms, enhances operational agility, and drives significant business value.
Resource Efficiency
As we’ve seen, Containers are surprisingly resource-efficient. They reduce overhead by sharing the kernel of the host operating system, allowing organizations to use resources more efficiently.
Due to the large reduction in overhead, system resources like CPU, memory, and disk space are used effectively. In the future, organizations may operate more containers on a single host thanks to the reduced resource footprint, which will result in cost savings and optimized infrastructure usage.
Density
A higher density of application instances may be run on a single host thanks to this efficiency, which also results in significant cost savings. Multiple container instances can survive on the same server due to containers’ lightweight design and kernel-sharing capabilities. This enhanced density is especially helpful in environments where making the most of available resources is a top priority. It implies that businesses can maximize their current hardware expenditures and attain higher application-to-hardware ratios.
Organizations looking to maximize infrastructure consumption might benefit greatly from the capacity to operate many containers concurrently.
Rapid Startup
Containers and agility go hand in hand. Due to the lack of a full OS boot, applications start up almost instantly and may be scaled up or down quickly in response to changing demand.
This rapid startup time is a game-changer for applications that need to respond swiftly to fluctuating workloads. Containers can be spun up and scaled quickly, ensuring that organizations can efficiently address dynamic demands, maintain optimal performance, and meet service-level agreements (SLAs).
Portability
Furthermore, the portability of containers is a game-changer. Applications and their dependencies are combined into a single self-contained entity by containers. This independence ensures consistent behavior across many environments, including development workstations, production servers, and cloud computing platforms.
Applications that are packed as containers can be readily deployed between various infrastructure environments, removing issues with compatibility and streamlining the deployment procedure.
Isolation
In terms of isolation, Container Technology gives a substantial advantage. Containers offer strong process-level separation while using the same host operating system kernel. Each container operates as a distinct entity and runs as a different process on the host. A secure and stable environment is created because of the isolation, which guarantees that programmes inside containers are not impacted by changes or problems in other containers.
Scalability
Another noteworthy aspect of Container Technology is scalability. Because containers are scalable, they enable businesses to quickly adjust to shifting workloads and expectations. Applications can scale up or down as necessary with the quick creation or removal of container instances. For businesses with variable workloads, this agility is priceless. Containers give businesses the ability to use resources more efficiently and keep performance at its best, even during instances of high demand.
DevOps and CI/CD integration
Containers are seamlessly integrated into DevOps procedures and Continuous Integration/Continuous Deployment (CI/CD) pipelines. Applications can be packaged in containers by developers, guaranteeing consistency throughout the development lifecycle. Container deployments can be automated by operations teams, resulting in quicker and more reliable software delivery. This collaboration between the development and operations teams drives the adoption of agile and DevOps ideas.
Security in Container Technology
Container Technology has revolutionized Software Development and Deployment, but tremendous power also comes with great responsibility. It is crucial to ensure the security of containerized applications to guard against potential threats and vulnerabilities.
Here are the best practices so you can keep your containers secure:

Best Practices for Securing Container Technology
Securing Images
- Start with Trusted Sources:
Official container images should be used as they are continuously maintained and security-audited. They should be obtained from reliable sources. - Verify Signatures:
Prior to deployment, confirm the integrity of container images and that they are signed. - Scan Images:
Images should be scanned using image scanning software to find flaws, malware, and configuration problems. - Image Hardening:
Remove unused components, services, and packages from container images to minimize potential attack surfaces.
Securing Registries
- Access Controls:
Implement stringent access controls for container registries to restrict who can upload and download images. - Use Private Registries:
To regulate image distribution and access, consider relying on private container registries. - Enable Authentication: To prevent unauthorized access, make it necessary for users to authenticate before accessing the registry.
Securing Deployment
- Limit Privileges:
Refrain from running containers as root. Least-privileged user accounts should always be used. - Isolation:
Use orchestration tools for containers to keep containers separate from one another and the host system. - Network Segmentation:
Implement network policies and firewalls to manage traffic between containers and pods by using network segmentation. - Runtime Protection:
To keep an eye out for suspicious activity and security risks in containers, use runtime security solutions.
Secure your host and Container Runtime
- Secure the Host OS: Patch and update the host operating system on a regular basis. To resolve vulnerabilities that might be exploited, security upgrades should be rapidly applied.
- Implement Access Controls:
Employ access controls and authentication procedures to prevent unauthorized access to the host system. Consider using multi-factor authentication and creating strong passwords to increase security. - Monitor Host Activity:
Use host-level monitoring to find out-of-the-ordinary or suspicious activity. Threats can be identified with intrusion detection systems (IDS) and intrusion prevention systems (IPS). - Apply Hardening Practices:
To reduce the attack surface, adhere to recommended host hardening techniques. Reduce potential points of exploitation by disabling unused services and functions.
- Regularly Back Up Data
Ensure that vital data on the host is regularly backed up. Having backups is beneficial in case of a security event or system breach.
Read our blog about the Best Docker Security Practices.
Using Thin, Short-Lived Containers to Reduce Your Attack Surface
- Adopt Minimal Images:
To lessen the attack surface on containers, use simple base images. - Single-Process Containers:
Create containers that only execute one process to lessen complexity and security risks. - Short-Lived Containers:
Promote the utilization of short-lived containers to reduce exposure to dangers.
Monitoring Container Activity
- Logging:
Enable logging at the container level to record activities and security incidents. - Centralized Logging:
Gather container logs into a centralized system for analysis via centralized logging. - Real-Time Monitoring:
Implement real-time monitoring to quickly identify and respond to security events.
Using Container Security Tools
- Security Scanning:
Utilize technologies for container image scanning to find vulnerabilities and incorrect setups. - Threat Detection:
Utilize threat detection techniques to keep an eye out for unusual activity in container activities. - Compliance Checks:
Automate compliance checks to make sure containers follow security guidelines.
Managing Secrets
- Secrets Management:
To distribute and preserve sensitive data securely, put in place a strong secrets management solution. - Encrypted Secrets:
To prevent unauthorized access, encrypt secrets both in transit and at rest. - Role-Based Access:
Implement role-based access control to limit who has access to secrets.
Challenges and Considerations in Container Technology
Although Container Technology has many advantages, it also has its own challenges that businesses must consider. These include avoiding vendor lock-in, maintaining security, managing resources, and handling orchestration complexity. It’s essential to evaluate your application’s specific needs, prioritize open standards, invest in the right expertise, and adapt processes to fully leverage the benefits of containerization. The following are a few important points to think about when facing these challenges:
Choosing the Right Container Technology
Challenge: The container ecosystem is huge, and many different platforms and tools are available. It can be challenging to choose the best ones for your particular needs.
Consideration: Based on your application’s demands, scalability requirements, and expertise available, evaluate container runtimes, orchestrators, and registries
Vendor Lock-In for container technology
Challenge: It may be tough to switch to other solutions if some container platforms and services lock you into their ecosystem.
Consideration: To prevent vendor lock-in, give open standards and compatibility a top priority. Select solutions that support portable containers.
Maintaining Container Security
Challenge: If improperly set up and monitored, containers might pose security vulnerabilities.
Consideration: Remember to employ runtime security tools, secure container images, and patch and update containerized apps on a regular basis.
Resource Management in container technology
Challenge: It might be difficult to efficiently distribute and keep track of storage, CPU, and memory resources across containers.
Consideration: Automate resource management and scaling based on demand by using container orchestration solutions like Kubernetes.
Orchestration Complexity in Container Technology
Challenge: Managing containers at scale necessitates orchestration tools, which can add complexity.
Consideration: To use orchestration platforms like Kubernetes efficiently, invest in training and knowledge, and for simplicity, think about managed Kubernetes services.
Limited Support for Legacy Applications
Challenge: Because of dependencies or design limitations, some legacy programmes could be difficult to containerize.
Consideration: Take into account techniques like containerizing components, utilizing VMs alongside containers, or converting traditional programmes to microservices.
Data Management in Container Technology
Challenge: Implementing backup and recovery plans and ensuring data persistence might be difficult in a containerized environment.
Consideration: To handle data in containers effectively, use external storage options, cloud-native databases, or stateful sets in Kubernetes.
Adapting Processes to Support Containers
Challenge: Adopting containers frequently necessitates modifying the methods used for development, testing, and deployment.
Consideration: To automate testing, streamline processes, and enable continuous integration and continuous deployment (CI/CD), it is important to promote a DevOps culture.
What are Use Cases for Containers?
Containerization technology has a wide range of applications and is at the forefront of modern software development. Here are several key use cases where containers offer significant advantages.






Microservices Architecture
Containers play a key role in enabling microservices architecture, which has become a popular software development methodology. Applications in this architecture style are split into separate, loosely coupled services. The ideal environment for any microservice is provided by containers.
They provide seamless orchestration, scalability, resource efficiency, and service isolation. Complex, distributed applications are easier to manage and evolve when using containers since microservices may be developed, tested, and scaled individually. Furthermore, containers fit into CI/CD and DevOps pipelines easily, allowing for continuous integration and deployment.
Multi-Tenancy
Containerization technology is a major benefit for multi-tenancy applications, which are instances of applications that serve various tenants or user groups. Containers provide strong separation across tenant environments, protecting data privacy and avoiding interference. By implementing resource allocation, you may ensure a fair distribution of CPU, memory, and storage resources among tenants.
Additionally, because containers allow for mobility, tenant instances can be easily moved between hosts or cloud providers as needed. Containers are a great option for multi-tenant environments because of their resource management and security features.
Application Deployment and Scaling
The deployment and scaling of applications have been transformed by containers. By putting dependencies and applications together, they guarantee consistency and lessen the “it works on my machine” issue. With containers, scaling applications is a breeze.
Orchestration technologies automate the process of spinning up new container instances to address surges in traffic. Applications can be kept up to date using rolling updates, which can be carried out without any downtime. When several containers may operate on a single server or cloud instance, the resource efficiency of containers optimizes the use of infrastructure.
Multi-Cloud Deployment
Containerization technology makes it easier to run apps in a hybrid cloud environment or across various cloud providers. Because they encapsulate dependencies and apps, containers are vendor-neutral and incredibly portable. Because of its mobility, cloud providers can be used concurrently or with ease, as vendor lock-in is reduced. Organizations can efficiently utilize their cloud resources to the fullest thanks to containers’ resource efficiency. Tools for container orchestration improve multi-cloud deployment by making load balancing and high availability easier.
DevOps Practices
By encouraging seamless communication between development and operations teams, DevOps practices take center stage in the world of container technology. By allowing developers to pack applications into containers, containerization simplifies the development pipeline. This allows for quicker and more dependable software delivery. These containers are then deployed consistently and automatically.
Applications are developed, tested, and deployed effectively with the help of DevOps techniques combined with containers. The software development lifecycle becomes more flexible and responsive as a result of the collaborative approach, which breaks through traditional silos between IT operations and development. Additionally, containerized apps benefit from DevOps practices, which improve their scalability, dependability, and maintainability, making them the perfect choice for contemporary, rapid development environments.
Case Studies of Container Technology
In the following case studies, we examine two transformational journeys made by IBM and PayPal to highlight how containerization technology has transformed their business models and opened the door for increased productivity and scalability. These interesting cases show how application container technology enables them to streamline processes, increase production, and adjust to changing and future market needs.
IBM: IBM Control Desk
The transformation of IBM Control Desk, a traditional IT service management software, into a microservices architecture utilizing Docker container technology is the subject of this interesting case study. Adopting cloud-native technologies without changing the product’s fundamental code was the biggest hurdle.
As a result, the application was divided into several components, each of which was given its own Docker image and then deployed inside a container. This strategy preserved the integrity of the product while achieving increased efficiency and the benefits of cloud-native solutions.
The journey of the IBM Control Desk emphasizes how crucial it is to identify independent modules inside an existing application and re-engineer build scripts to produce a containerized microservices architecture. Rigorous testing was essential to ensure enhanced performance and scalability without introducing unanticipated difficulties.
This case study provides insightful information for businesses considering similar changes. Click here to learn more.
PayPal
A major player in the online payment industry faced the daunting task of handling 200 user payments per second across PayPal, Braintree, and Venmo. However, their struggle lay in the slow deployment and maintenance processes caused by operating on diverse architectures and cloud platforms. This resulted in delayed transaction processing times and user dissatisfaction.
Docker Enterprise, a top containerization platform, provided PayPal with a game-changing solution. Docker Enterprise enabled centralized container technology administration, improved operations, and simplified their approach to application delivery.
PayPal completely revamped its deployment processes by continuously packaging its existing applications using Docker container technology. The productivity of developing, testing, and deploying applications impressively increased by 50% as a result.
PayPal is now able to handle more than 8 billion transactions annually thanks to this shift. This case study demonstrates how adopting containerization, in particular Docker Enterprise, may completely transform how payments are processed in the quick-moving online payments sector. Click here to learn more about this in detail.
Conclusion of Container Technology
The revolutionary concept of Container Technology is changing the way we build, deploy, and manage applications.
Containers have several benefits, such as resource efficiency, quick startup, portability, improved isolation, scalability, and easy integration with CI/CD and DevOps pipelines. Because they guarantee consistent behavior across several contexts and solve the “it works on my machine” problem, they have completely changed the way software is deployed.
Although application container technology has many benefits, it’s crucial to recognize the challenges and considerations that must be considered. These include selecting the appropriate container technology, like Docker container technology, preventing vendor lock-in, preserving container security, resource management, orchestration complexity, and support for legacy applications. Addressing these challenges is essential for successful containerization initiatives.
Remember that you don’t have to do it alone as you start your journey with Container Technology. ClickIT is here to provide the expertise and support you need to navigate the complexities of Container Technology. Our team of professionals is prepared to help you realize the full potential of containerization technologies, whether you’re seeking guidance, consultation, or implementation of tools like, Docker container technology.
Container Technology FAQs
Installing containerization tools like Docker container technology and exploring introductory tutorials and documentation are good places to start. A fantastic approach to learning is to experiment with simple applications.
Yes, containers can run on various cloud platforms, local servers, development workstations, and more. They are also quite portable. They offer uniformity between environments.
To ensure high availability, load balancing, and automated deployments in complicated containerized applications, orchestration solutions like Kubernetes help manage and grow Containers.
Container Technology is ideal for cloud-native applications, microservices architectures, and quick scaling scenarios.
When people discuss containers, Docker container technology is frequently the first name that comes to mind. Many developers and organizations now consider Docker the preferred containerization solution due to its broad appeal and influence on containerization technologies. It offers a complete platform for building, packaging, and distributing containers.