Ansible vs Terraform are the two most popular tools in the DevOps space, serving distinct roles according to statista. Ansible is a configuration management and IT automation tool that simplifies repetitive tasks and uses human-readable YAML syntax making it a good choice for beginners as well as advanced users.
Terraform excels in infrastructure provisioning. It helps organizations provision and orchestrate tasks declaratively in a multi-cloud environment. Many organizations add both to their DevOps toolchain to enjoy a comprehensive and efficient IT automation workflow. This blog deep-dives into the Ansible vs. Terraform debate to help you understand the difference between Ansible and Terraform.
- Ansible vs Terraform
- What it Infrastructure as Code
- What is Ansible?
- Ansible Use Cases
- What is Terraform?
- Terraform Use Cases
- Differences Between Ansible vs Terraform
- How to Use Terraform and Ansible Together?
- Conclusion
- FAQs
Ansible vs Terraform
| Ansible | Terraform | |
| Purpose | Primarily used for configuration management | Primarily an infrastructure provisioning and orchestration tool |
| Type of Tool | Configuration Management and Automation tool | Infrastructure as Code (IaC) tool |
| Syntax and Language | Uses YAML for Playbooks | Uses HCL for defining infrastructure as code |
| Execution Model | Push-based model | Pull-based model |
| Lifecycle Management | Not designed for full infrastructure lifecycle management | Supports full lifecycle management |
| Capabilities | Configuration management, application deployment, task automation, and some orchestration capabilities. | Infrastructure provisioning, orchestration, and management of cloud resources, including support for multi-cloud environments. |
| Packaging and Templating | Uses playbooks and roles for organizing and packaging configurations. Supports Jinja2 templating for dynamic content. | Uses modules for organizing and packaging infrastructure code. HCL allows for the definition of reusable and modular components. |
What is Infrastructure as Code?
The advent of Infrastructure as Code (IaC) has revolutionized the infrastructure management space. IaC enables organizations to provision and manage the IT infrastructure using code.
IT resources are provisioned programmatically using declarative or imperative scripts, offering IT automation, version control, and collaboration while eliminating manual errors. It enhances scalability and accelerates deployment cycles. This shift rightly aligns with modern software principles and enables organizations to evolve towards more agile, efficient and automated IT operations. It also brings Terraform vs Ansible into the picture.
Both Ansible and Terraform contribute to a broader goal of automating and managing IT infrastructure.
When it comes to Ansible vs Terraform, Ansible is a configuration management tool, while Terraform is an infrastructure provisioning tool. Together, they address different aspects of the DevOps lifecycle. This collaboration enables organizations to benefit from the strengths of each tool and adopt a holistic approach to IT automation. Understanding the difference between Ansible and Terraform enables organizations to fully leverage their capabilities.
What is Ansible?
Before delving into the ansible vs terraform debate, it is important to understand how each tool works. Ansible is a popular open-source IT automation and configuration management tool that enables users (like developers, system administrators, and architects) to streamline and simplify IT operations. Be it software installation, application deployment, or configuration management, users can automate system administration tasks across a large number of devices using Ansible.
Ansible is written in Python. It uses human-readable language that makes it easy to use and without a big learning curve. With minimal moving parts, Ansible brings security and reliability onto the plate. It is easy to use as there is no custom security infrastructure or agent system.
What are Ansible’s Key Features?
- Agentless: One of Ansible’s key features is its agentless architecture. With Ansible, you don’t need to install agents or any other software on the target machines. Ansible connects to target machines and controls them using SSH (Secure Shell) or other remote protocols, making it less intrusive and easier to manage.
- Playbooks: Ansible uses Playbooks to define and automate the infrastructure. A Playbook is a configuration file in YAML format that describes a series of tasks and their dependencies.
- Ad-hoc Commands: In addition to Playbooks, you can use Ad-hoc commands to perform quick tasks such as making a one-time change, checking the system status etc.
- Roles: Ansible allows you to organize and reuse the content of Playbooks using Roles. By organizing a set of variables, files, or tasks, you can easily manage and share automation code.
- Modules: Ansible uses Modules to interact with systems and perform tasks such as file manipulation, package management, and service management. Ansible offers many built-in modules and allows you to create custom modules.
- Idempotent: Ansible allows you to run a Playbook multiple times without causing unwanted changes to the system when it is in the desired state.
- Inventory: Ansible manages the list of target systems called inventories. Inventories can be defined in a simple text file or use scripts or plugins to generate dynamic inventories.

Read the blog on the best practices of Ansible
Ansible Use Cases
| Ansible Use Cases | ||
| Configuration Management | Enforce and maintain consistent configurations across server and network devices. | |
| Application Deployment | Automate the deployment of applications and services. | |
| Infrastructure Provisioning | Automate the creation and provisioning of infrastructure resources. | |
| Integrate into CI/CD workflows | Automate build, test, and deployment processes in a CI/CD pipeline. | |
| Security Compliance and Patch Management | Enforce security policies and apply system patches. | |
| Orchestration of Complex Workflows | Coordinate and orchestrate complex tasks involving multiple servers and services. | |
| Inventory Management | Manage and organize an inventory of infrastructure assets. | |
| Disaster Recovery | Automate disaster recovery processes. | |
| Logging and Monitoring Configuration | Automate the configuration of logging and monitoring tools. | |
| User and Access Management | Automate user provisioning and access management. | |
| Database Operations | Automate database provisioning, configuration, and maintenance. | |
| Networking Tasks | Automate network-related tasks on routers, switches, and firewalls. | |
What is Terraform?
Terraform is a popular infrastructure as Code from HashiCorp, that enables users to define and provision IT infrastructure resources using a declarative configuration language. Mitchell Hashimoto created the tool in 2014 in the Go language.
The tool allows you to define your infrastructure resources, such as servers, networks, and storage, in a configuration file. Terraform interprets this file and automates the process of creating, managing, and updating the corresponding infrastructure in various environments.
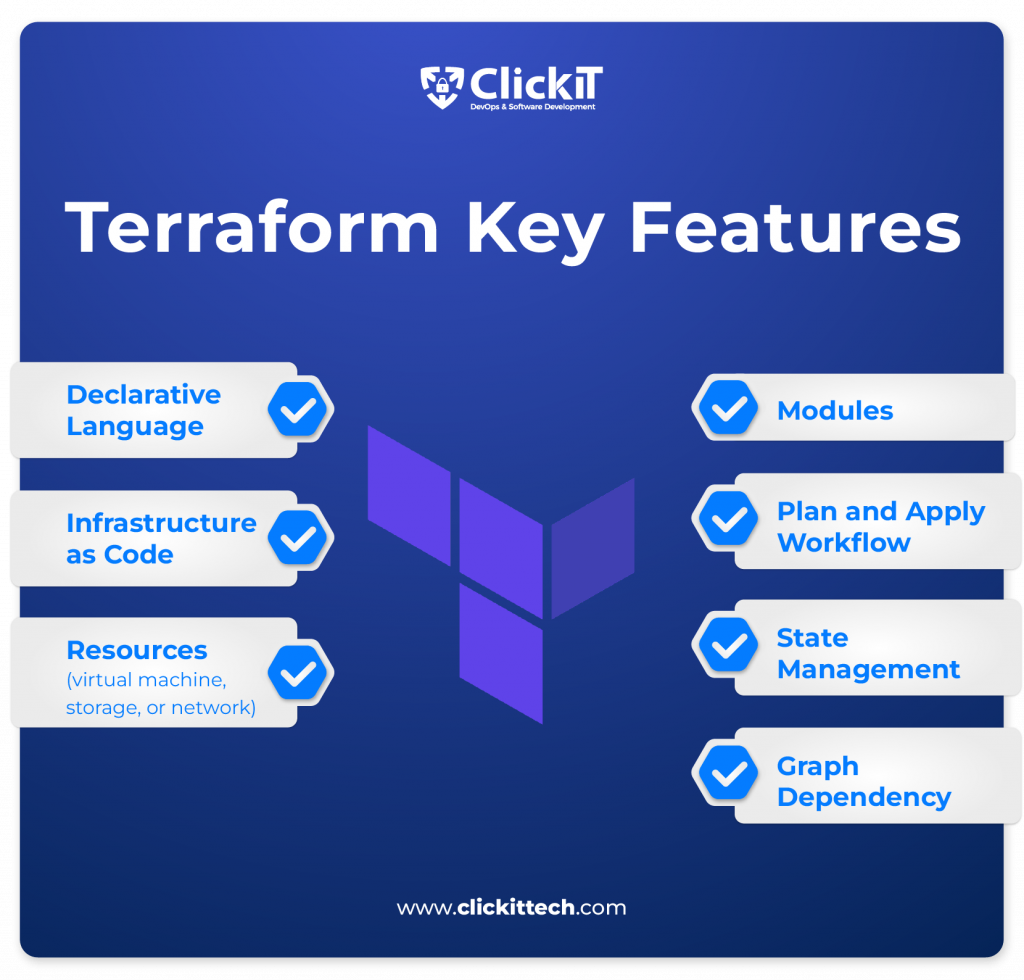
What are Terraform’s Key Features?
- Declarative Language: Terraform uses a high-level declarative configuration language called the HashiCorp Configuration Language (HCL) to define a system’s desired state. You just need to describe the infrastructure, and the tool will determine the required steps.
- Infrastructure as Code: Terraform enables you to treat the infrastructure as code. It means you can version control the infrastructure configurations, collaborate easily, reuse code and efficiently track changes to infrastructure over time.
- Resources: In Terraform, a resource represents an infrastructure component such as a virtual machine, storage or network defined in a configuration file.
- Modules: A module is a self-contained unit of Terraform configuration for parameterizing infrastructure components. This allows you to organize and reuse configurations.
- Plan and Apply Workflow: Terraform uses a `Plan and Apply Workflow’, a two-step process to perform infrastructural changes. While the `Terraform Plan’ examines the configuration and provides the changes being made, the `Terraform Apply’ feature executes those changes. So you can preview changes before applying them to the infrastructure.
- State Management: Terraform uses a state file to keep track of the state of the infrastructure so that you can plan and apply changes only to the resources that require updating.
- Graph Dependency Resolution: Terraform creates a dependency graph based on the configuration to determine the right order to create or modify resources. This will eliminate resource dependency issues.
Read our blog Terraform vs CloudFormation, to learn more about this debate
Terraform Use Cases
| Terraform Use Cases | ||
| Multi-Cloud Deployment | Deploy and manage infrastructure across multiple cloud providers. | |
| Infrastructure Provisioning | Automate the creation and provisioning of infrastructure components. | |
| Environment Standardization | Ensure consistent configurations and standards across development, testing, and production environments. | |
| Container Orchestration | Automate the deployment and scaling of containerized applications. | |
| Network Infrastructure Configuration | Automate the configuration of network components such as virtual networks, subnets, and firewalls. | |
| Application Stacks Deployment | Deploy and manage complex application stacks consisting of multiple interconnected components. | |
| Serverless Architecture | Automate the deployment of serverless functions and services. | |
| Immutable Infrastructure | Adopt immutable infrastructure practices by rebuilding and redeploying infrastructure components instead of modifying existing instances. | |
| Hybrid Cloud Deployments | Manage infrastructure across both on-premises data centers and public cloud environments. | |
| Collaborative Development Environments | Facilitate collaboration by providing developers with a standardized and automated way to create development environments. | |
| Logging and Monitoring Infrastructure | Automate the deployment and configuration of logging and monitoring tools. | |
| Disaster Recovery Planning | Define and automate the creation of infrastructure components necessary for disaster recovery. | |
Read our blog on the 24 Terraform best practices

Difference Between Ansible vs Terraform
Here are some of the key differences concerning Ansible vs Terraform based on the following criteria:

It is not always about Ansible vs Terraform or Terraform vs Ansible. They perform similar tasks as well. Here are some of the similarities between Terraform and Ansible.
Ansible vs Terraform: Purpose
Ansible is primarily designed for infrastructure configuration management. However, it is also used for infrastructure provisioning, application deployment automation, and task orchestration. Terraform is a basic IaC and orchestration tool that can also perform configuration management.
Ansible vs Terraform: Type of Tool
Ansible is configuration management software, while Terraform belongs to the Infrastructure as Code (IaC) category. This is a key differentiator in the Ansible vs. Terraform discussion.
Ansible vs Terraform: Syntax and Language
Ansible runs in Python. Most Linux distributions contain Python libraries, making installing and setting up the tool easy. It uses Playbooks to deploy and manage nodes. A playbook is a YAML-formatted configuration file that humans find easier to read and write than JSON or XML. Using Playbooks, you can orchestrate steps in a specific order or launch tasks asynchronously/synchronously. The syntax is minimal in YAML format.
When it comes to execution, Ansible runs Playbooks from top to bottom, and the same is true for tasks within each play. You can create modules in any language provided that they return data in JSON format.
Terraform uses a high-level configuration language Hashicorp Configuration Language (HCL). HCL is easy to read and understand. The syntax contains fewer elements and is easy to follow. Terraform also supports JSON format.
Ansible vs Terraform: Execution Model
It follows a push-based approach wherein the control machine pushes the configurations of the target machines. Ansible is executed from the control node when a user runs an Ansible playbook command. The control node pushes Ansible Modules to the managed machines and executes them over SSH. Once Ansible completes the task, it removes them.
Once the task is done, Ansible removes them. These modules are idempotent, meaning they don’t change when the target system is already in the desired state. Ansible operates without a separate state file
The main difference between Terraform and Ansible is that Terraform uses a Pull-based model wherein the clients pull the configuration and execute the plan to provision the infrastructure. Users can run the ‘terraform state pull’ command to manually download the state from the current location and update the local copy. Then, the system is updated to the desired state. Terraform maintains a state file that keeps track of the current state of the infrastructure.
Ansible vs Terraform: Lifecycle Management
Ansible supports configuration management but is not designed for full infrastructure lifecycle management. By default, Ansible assumes immutable infrastructure and automatically applies configurational changes to the target machines.
Terraform supports lifecycle management, including infrastructure provisioning, updating, and destruction. By supporting lifecycle arguments, Terraform allows users to define custom rules for creating or destroying a resource. This will help you to eliminate the risk of specific resources changing the infrastructure and also minimize downtime based on the needs of a resource.
Ansible vs Terraform: Capabilities
Ansible is popular for configuration management tasks. It also performs application deployment, task automation, and orchestration capabilities.
Terraform stands tall in the infrastructure provisioning space with capabilities including orchestration and management of cloud resources and support for multi-cloud environments.
Ansible vs Terraform: Packaging and Templating
Ansible uses Playbooks and roles to organize and package configurations. It supports Jinja2 templating for dynamic content.
Terraform uses modules to organize and package infrastructure code. HCL allows you to define reusable and modular components.
How to Use Terraform and Ansible Together?
It’s not just Ansible vs Terraform. Using Terraform and Ansible is a common practice in a DevOps workflow. Considering the fact that one tool excels in infrastructure provisioning and the other in configuration management, you get the best of both worlds.
a) Using the Ansible Provider in Terraform
- Define infrastructure with Terraform: Define the infrastructure components you want to provision using Terraform. Write Terraform configuration files to describe the state of your infrastructure.
- Provision Infrastructure: Run Terraform commands to initialize, plan, and apply the changes to your infrastructure.
- terraform init
- terraform plan
- terraform apply
- Use Terraform Output: Output relevant information from the Terraform state such as IP Addresses, instance IDs or other resource attributes that Ansible will use during the configuration.
- Configure with Ansible: Write Ansible Playbooks (in YAML) to configure the provisioned infrastructure and define tasks to be executed on hosts.
- Run Ansible Playbook: Run Ansible Playbooks against the provisioned configuration by providing required connection parameters such as SSH or remote user.
- Integrate Ansible with Terraform: To streamline this process, integrate Ansible with Terraform using the `local-exec’ provisioner in Terraform so that Ansible playbooks can be triggered when Terraform applies changes to the infrastructure.
- Destroy Infrastructure: When you no longer need the infrastructure, destroy it using Terraform.
- terraform destroy
This command terminates all resources managed by the current Terraform project. Terraform will provide the details of the resources that will be terminated. Make sure to carefully check the displayed resources and then confirm the termination, as this action cannot be undone later.
- Cleanup: As a best practice, clean up any remaining state files or resources.
b) Deployment of stacks in new infrastructures created by Terraform
When you integrate Terraform with Ansible, you can automate the deployment of stacks in new infrastructures created by Terraform. Here are the steps to do so:
- Write Terraform Configuration: Use Terraform to create infrastructure components you want to provision while including the necessary outputs Ansible will be using.
- Provision infrastructure with Terraform: Run Terraform commands to initialize, plan, and apply the changes to your infrastructure.
- terraform init
- terraform plan
- terraform apply
- Capture Terraform Output: Capture Terraform output that can be used by Ansible.
- Write Ansible Playbook: Create an Ansible playbook to configure and deploy your application stack while referencing the output values obtained from Terraform in the playbook.
- Run Ansible Playbook: Run the Ansible playbook to execute tasks against the provisioned infrastructure, passing the required parameters.
- Integrate Ansible with Terraform: To streamline this process, integrate Ansible with Terraform using the `local-exec’ provisioner in Terraform so that Ansible playbooks can be triggered when Terraform applies changes to the infrastructure.
- Verify and Monitor: Verify that the stack is deployed successfully and monitor the application and the infrastructure for any issues.
- Destroy Infrastructure: When you no longer need the infrastructure, destroy it using Terraform.
Conclusion of Terraform vs Ansible
In the Ansible vs Terraform debate both have the capabilities to perform similar tasks, they are designed with different purposes in mind. Ansible excels in configuration and automation tasks and is popular for its simplicity and versatility. The push-based model and YAML syntax make it user-friendly.
On the other hand, Terraform focuses on infrastructure provisioning. With its declarative language, state management, and multi-cloud provisioning, Terraform is popular among organizations that emphasize infrastructure orchestration. While they address different aspects, you can combine them to bring the best of both worlds.
While Terraform handles infrastructure provisioning, Ansible manages configuration management for efficient and comprehensive IT automation. It’s not about Ansible vs Terraform or Terraform vs Ansible but Terraform and Ansible.
Terraform vs Ansible FAQs
With its simplicity and versatility, Ansible is more suitable for day-to-day automation tasks such as configuration updates, system management, and application deployments. Terraform can be used for less frequent tasks, such as defining and managing infrastructure configurations.
Ansible offers modules and features for secret management. For instance, Ansible Vault encrypts sensitive data in Playbooks. Terraform does not have a built-in feature for secret management, so you’ll have to use external services.
Both tools perform well when it comes to managing network configurations. Ansible offers modules to interact with network devices and automate networking tasks. Terraform also allows users to define and provision virtual networks, subnets, and firewall rules.
Yes, both tools can be used to manage on-premise environments. They are not confined to cloud environments.
It depends on the use case. Ansible is better for configuration management and app deployment, while Terraform excels at provisioning and managing infrastructure as code.