I show how to build a multi-tenant SaaS architecture on AWS that consolidates all customers into one environment for better scalability.
I leverage Kubernetes with Amazon EKS to orchestrate containerized microservices, isolating each tenant in separate namespaces for security and efficient resource utilization. Each tenant is provided a dedicated database (e.g., its Amazon RDS instance) to ensure strict data separation and compliance, following a single-tenant database strategy for maximum data security.
I also emphasize cost optimization using serverless components and Spot Instances to maximize efficiency.
Equally important is enforcing robust security best practices, like IAM role segregation, encryption, and web application firewalls (WAF) to safeguard each tenant’s data and services . Tenant management is streamlined through automation using AWS tools (CloudFormation, Lambda, etc.) to quickly onboard new tenants with minimal manual effort.
Additionally, I harness AI-powered monitoring via Amazon CloudWatch AIOps and DevOps Guru to proactively detect anomalies and keep each tenant’s services running smoothly together; these strategies form the backbone of a robust, secure, and cost-effective multi-tenant SaaS platform on AWS.
Are you tired of creating different application code sources for each customer or tenant, wasting money, or creating multiple environments across different customers? This Enterprise SaaS Architecture in AWS is for you.
The next architecture will help unify all your customers’ environments into one unique environment and source code, which is called multi-tenant architecture.
- What is Enterprise SaaS Architecture?
- Key Components of Enterprise SaaS Architecture on AWS
- Implementing Multi-Tenancy in Enterprise SaaS
- Tenant Management
- Best Practices for Enterprise SaaS Architecture on AWS
- Enterprise SaaS Architecture FAQs
What is Enterprise SaaS Architecture?
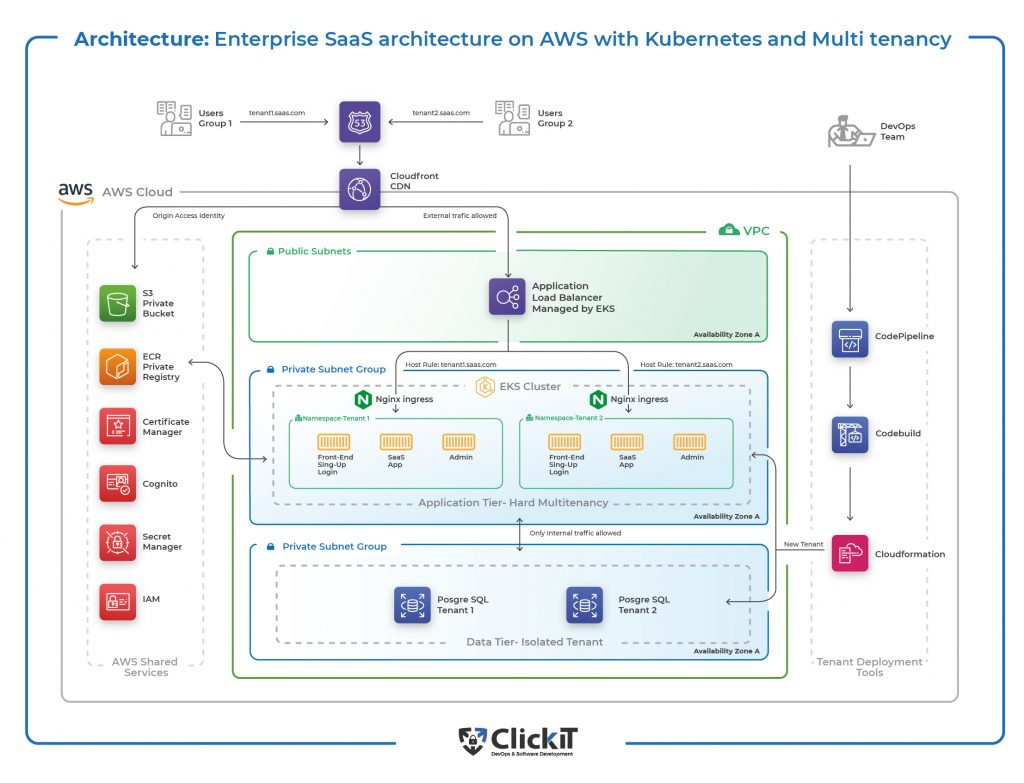
You will have two tenants that are pro for today’s architecture. Those tenants will obviously hit Route 53, which is the one to roll the domain or the subdomain in this case. Then, it will hit the CloudFront CDN service, which you know holds or clears all the static content from videos in the CSS or a front-end application.
If you go more deeply into the stream, you will hit the application load balancer, the latest application LB from Amazon Web Services. This can help you upload HTTP requests and utilize AWS-shared services like Certificate Manager and Amazon Certificate Manager.
Then, they’ll be routed between the two Ingress or namespaces, which will be detailed later inside the EKS cluster. This EKS cluster is a multi-tenant architecture, but going deeply into the database, the layer will be a single-tenant database approach.
A multi-tenant architecture consolidates customers into one codebase and environment, reducing overhead while improving scalability. The 2025 approach emphasizes:
- Cost optimization via serverless and spot instances.
- Global resilience with AWS Local Zones and edge computing.
- AI/ML integration for tenant-specific personalization.
Key Components of Enterprise SaaS Architecture on AWS
The Enterprise SaaS Architecture Network on AWS
Now, let me tell you about the SaaS Network on AWS. As you know, Amazon recommends having a public subnet and a private network as a best practice.
You will hold the ALB in the public subnet; in the private network, you will have the AKS cluster, the namespaces, and microservices, as well as another private network that will call the databases.
That’s the best way to create an Enterprise SaaS architecture diagram. On the left side, you will have all the AWS shared services outside the public and private networks in the AWS cloud.
Microservices, Containers and Docker
You will have three microservices. In this case, you will have three applications in one microservice: the front-end web application, the signup, and the login. Then, you will have the second microservice, the SaaS application per se, the whole ecosystem, and the admin dashboard, which is very common in SaaS architectures. This namespace will be mimicked to namespace two or tenant two, namespace three, four, etc.
It’s important to mention that microservices bring many benefits to software development, including flexibility, portability, and speed. So, it’s imperative that besides adding an EKS cluster or using Amazon ECS, Fargate, or another cloud provider, you must use microservices for your development testing and production and, if you are growing, use a content management system like an EKS cluster.
The web stack we will use for this SaaS architecture diagram is Vue.js, and all the back-end development will be Node.js with the Express framework. Also, all the microservices will be updated from the ECR, Amazon’s container repository system.
Lastly, the login will interact with Cognito. You can integrate when you log in instead of creating your login. You need a small application and combine it with Amazon Cognito, which will bring some benefits when developing software. So that’s a good practice as well.
Amazon ECS vs EKS: Read the complete comparison to choose the best container service.
AI-Powered Monitoring & Logging
- Amazon CloudWatch AIOps: Automatically detect tenant-specific anomalies (e.g., sudden API error spikes in Tenant 3’s namespace) using ML models trained on your historical data. Pair it with CloudWatch Metric Math to create custom metrics like
CostPerTenantorAuthLatencyByRegion. - Amazon DevOps Guru: Proactively identify misconfigured resources (e.g., an over-provisioned RDS instance for a low-usage tenant) and recommend fixes. Use its Insights Engine to predict risks like ALB throttling during tenant onboarding.
- Centralized Logging: In plain English, ship logs to OpenSearch Serverless and use Generative AI-powered Query Assistant to troubleshoot issues like “Why did Tenant 5’s microservice crash at 2 AM?
Implementing Multi-Tenancy in Enterprise SaaS
Application Layer Multi-Tenancy
In this enterprise SaaS architecture, you have tenants one and two; every tenant will go to the Nginx ingress controller and the ingress controller two. Remember that every Namespace should have its own Nginx controller.
Now, how is this environment isolated?
That’s why you have to configure the namespaces one, two, and three in Kubernetes, which are the ecosystems that isolate different tenants. These, with a hand of the IAM roles, the port security, and some other security roles, will help you have a silo model, which that’s the standard label from Amazon Web Services, having an isolated environment per each tenant or namespace.
Amazon Web Service has released an LB controller service, which will replace the Nginx controller. But there is an LB controller, which will be under replacement from the Nginx ingress controller.
But this is a little complex. If you require DevOps assistance, you can reach out to us, and we will help you with a dedicated DevOps Engineer in this particular case or with all your SaaS architecture diagram and DevOps practices.

Database Layer Multi-Tenancy
In this setup, there is no multi-tenancy. Instead, we use a single-tenant architecture with isolated databases for PostgreSQL Tenant One and PostgreSQL Tenant Two. These databases are hosted on Amazon RDS, which runs the PostgreSQL engine. This approach is crucial for maintaining data security, ensuring that sensitive information is not stored in a shared database.
For example, if Tenant One could access critical data from Tenant Two, it could lead to security breaches and regulatory compliance issues. To mitigate this risk, we strictly separate databases per tenant. While this approach has some drawbacks, such as increased costs and more complex database management, it is necessary, especially for industries like FinTech, banking, and security systems. These sectors typically require a strict single-tenant architecture to meet security and compliance standards.
Alternatively, a multi-tenant approach could be used by assigning a unique tenant ID to each customer. This can be implemented at different levels:
- Per schema: Each tenant has a separate schema within the same database.
- Per table: A shared table structure with a tenant ID column to differentiate records.
- Single user table with tenant ID: Common in MVPs, startups, and SaaS platforms looking to streamline tenancy management.
Many early-stage SaaS companies and startups opt for a shared table with a tenant ID, which is often sufficient for small to medium businesses. However, as a company scales into the enterprise space, proper data isolation becomes a priority to ensure security, compliance, and performance.

Tenant Management
Creating New Tenants
Orchestrating new tenants in your enterprise SaaS architecture requires extensive DevOps expertise. To create new tenants for the next steps, you will need CodePipeline, Amazon Code Build, and Amazon CloudFormation. Usually, it starts with scripting using DevOps or tenant deployment tools.
- Create the new subdomain for tenant two from tenant three using Route 53.
- Create some entries in the LB because there will be a new tenant.
- Get a new namespace, namespace three, with the pertinent routes to the microservices. The microservices need to be updated from the ECR. There will be a new tenant and microservices; you must also update the EKS cluster.
Tenant Isolation and Resource Allocation
- AWS Tags: Enforce mandatory tags (e.g.,
tenant-id,env) for cost allocation. - Quotas: Use AWS Service Quotas to limit tenant resource consumption.
After setting up the application layer, you must provision an RDS environment for tenant-specific namespaces. For instance, in the case of tenant three, you can deploy Amazon RDS with either MySQL or Postgres, ensuring that each tenant has its isolated database.
Additionally, don’t forget to configure the appropriate domain for the new tenant. This might involve adding a new SSL certificate, and you can leverage Python scripting to streamline this process.
Alternatively, you could automate these tasks by using a RESTful API. Tools like Amazon API Gateway, Lambda, and languages like Python or Node.js can help manage tenant-specific resources efficiently.
Best Practices for Enterprise SaaS Architecture on AWS
When implementing an Enterprise SaaS architecture, it’s crucial to follow a set of best practices to ensure scalability, security, and efficiency:
Data Isolation
Always ensure data isolation between tenants by using separate databases or schemas for each tenant. This minimizes the risk of data leakage and improves security, especially for industries with strict compliance requirements like finance and healthcare.
Automate Tenant Provisioning
Automation tools like AWS CloudFormation, CodePipeline, and Lambda can be used to streamline the provisioning of new tenants. This reduces manual effort, speeds up the process, and minimizes errors.
Monitor and Scale
Leverage AWS tools like CloudWatch for real-time monitoring and Auto Scaling for dynamically adjusting resources based on tenant usage patterns. This ensures optimal performance without overprovisioning.
Optimize Costs
Use AWS cost management tools to monitor resource utilization and optimize your infrastructure to avoid unnecessary costs. Implement a tagging strategy to track expenses per tenant. Spot Instances use the EKS Spot Termination Handler for stateless microservices and Savings Plans like Committing to 3-year terms for EKS, RDS, and Lambda.
Security Best Practices
Ensure proper IAM role segregation, encryption, and use of AWS security services like Cognito, GuardDuty, and WAF to safeguard your SaaS environment from threats.
Following these best practices, you can build a robust, secure, cost-effective, multi-tenant SaaS architecture on AWS.
I’m hoping that you understand how the pieces required to create a multi-tenant architecture from the application layer, and there is a layer along with how to create a new tenant, which if you look in the network or Google, is complex to find what are the missing pieces, which are just a few of the
Lastly, contact us to learn more about how ClickIT helps SaaS Enterprises run and develop DevOps practices in the cloud or if you’re just curious about hiring a nearshore Software Developer in the same timezone.

Enterprise SaaS Architecture FAQs
Enterprise SaaS (Software-as-a-Service) architecture refers to the overall structure and design of a cloud-based software system that serves enterprise needs. It typically leverages a single application instance to serve multiple customers (tenants) efficiently, using cloud infrastructure to ensure scalability, easy updates, and maintenance.
In practice, an enterprise SaaS architecture includes multi-tenancy, integration with other services, and design principles that ensure high availability, security, and performance for all users.
An enterprise SaaS architecture offers a range of benefits, including scalability, cost efficiency, accessibility, security, and flexibility, making it a compelling choice for businesses looking to leverage modern, efficient software solutions.
To build an enterprise SaaS architecture, define precise requirements and select an appropriate technology stack. Design a scalable and secure architecture focusing on multi-tenancy, integration capabilities, and a user-friendly experience. Prioritize security measures, data management strategies, and compliance with regulations.
AWS provides a robust and flexible foundation for building and scaling SaaS applications, offering a combination of global reach, security, cost efficiency, and services that cater to diverse business needs.
Authentication & Authorization: Implement strong user authentication (e.g., multi-factor login) and role-based access control to ensure only authorized users access sensitive features.
Data Encryption: Encrypt sensitive data both in transit (using SSL/TLS) and at rest in databases. This protects user credentials, personal information, and payment data from unauthorized access.
Network Security: Use firewalls, VPNs, and intrusion detection/prevention systems to secure the network layer. Isolate application tiers in private subnets and employ security groups to limit traffic.
Disaster Recovery & Backups: Maintain regular data backups and a disaster recovery plan. This ensures business continuity and data protection in case of outages or breaches.
Compliance and Monitoring: Adhere to industry regulations (e.g., GDPR, HIPAA, PCI-DSS) and conduct regular security audits. Continuous monitoring and logging help detect vulnerabilities or suspicious activities early.